Keeping a Hand on the Tiller: A Threat-Led Approach to Maritime Cyber Risk
A threat-informed strategy can help maritime organisations improve security decision-making.
The pandemic has had a large impact on global supply chains. Ports and vessels have been especially impacted due to reductions in operations, crew disruption, and backlogs at crucial ports. As global supply chains continue to recover, there is an ongoing risk that maritime organisations will increase their risk acceptance in an effort to reach pre-pandemic levels as soon as possible. The cyber security of maritime organisations is therefore more critical than ever. This challenge must be met head on to protect not just the maritime sector, but also the far wider supply chain that remains highly reliant on cargo and shipping networks.
This means that the cyber security of maritime infrastructure has quickly transitioned from a mere IT problem to what is now a much larger and more systemic concern. This was demonstrated only recently, when a Belgian port terminal became the latest entity to shut down operations as a result of a cyber attack.
The International Maritime Organization has rightfully called for a renewed focus on cyber risk in response to these growing concerns. Yet, simply increasing cyber security spending or adopting static cyber risk frameworks is unlikely to seriously counter the threat at hand.
This is because the maritime sector faces a challenge of adaptation with the cyber threat landscape growing in both complexity and scale. Russia’s invasion of Ukraine creates an elevated cyber threat for various Western entities. Maritime organisations could certainly be targeted given the sector’s obvious connection to national security. Yet, the cyber threat landscape extends far beyond Moscow and also includes several emerging cyber threats (such as ransomware). These are ultimately distinct from many of the traditional security concerns within the sector. Moreover, while the supply chain discussion within cyber security has understandably focused on the SolarWinds compromise, beneath this is a wider spectrum of supply chain threats spanning both espionage and cybercriminal threats.
Maritime organisations must therefore make a concerted commitment to engage with developments in the threat landscape.
A Broadening Cyber Threat Landscape
While the maritime threat landscape has undoubtedly widened, the sector has traditionally focused on state espionage threats. This has been for good reason: threats emanating from Russian and Chinese state agencies represent the top tier of cyber threats. Not only are they well resourced, but they have also demonstrated an observable interest in maritime organisations.
China, for instance, is highly active in conducting cyber operations against entities linked to South China Sea tensions. Likewise, the threat group known as APT40 conducts espionage with an emphasis on maritime issues and naval technology – likely in support of China’s ambition to establish a blue-water navy. The recent AUKUS agreement highlights Australia’s increasing interest and access to advanced nuclear submarine technology, and this will likely increase China’s cyber operations against maritime organisations in the country as well as those supporting AUKUS globally. Ultimately, states utilise cyber operations to realise their geopolitical aims, with maritime entities therefore likely to remain a high priority target.
In the coming years, cyber espionage threats will broaden beyond Russia, China, Iran and North Korea. Vietnam is one example of a state that has also built up an impressive cyber capability and previously targeted maritime agencies, sea construction entities and shipping enterprises. Maritime entities will therefore have to increasingly account for a host of emerging espionage actors as more states turn to cyber operations to achieve geopolitical and military goals.
While the espionage threat to the maritime realm is not going away anytime soon, the threat is broadening across other vectors.
Ransomware is now causing devastating impact and is now perceived as a matter of national security. Several factors explain this shift, although the main driver has been operations that are increasingly sophisticated and targeted. Rather than deploying ransomware on the first systems found (as was often the case), attackers have adopted a more targeted approach that focuses on core domain infrastructure and the systems that allow a network to function.
The impact of these operations is already being felt within the maritime sector. An attack on South African port infrastructure in July 2021 highlighted the disruption these incidents can have on cargo shipments while a similar incident also occurred at the Port of Kennewick in Washington. The targeting of service providers that have footprints in multiple ports and supporting infrastructure has proven to be very impactful. This has resulted in vessels temporarily having to avoid ports due to disruption, and in the worst cases, diverting to a different destination entirely.
Cyber threats are also increasingly targeting operational technology (OT) – the systems that interact directly with physical processes, machinery and infrastructure. This could include cargo loading infrastructure within ports and bridge navigation and communication systems. OT systems tend to be far more niche, and it has long been assumed that only state espionage groups with specialist skills would be able to target them. However, several high-profile criminal groups have included OT processes on ransomware kill lists, including CLOP, DoppelPaymer, LockerGoga, Maze, MegaCortex, Nefilim, HelloKitty, and SNAKEHOSE (among others).
Relatively unsophisticated threat groups are also increasingly targeting OT systems. These operations are conducted by threat groups that are motivated by a range of ideological, egotistical or financial objectives. These compromises are typically much less sophisticated and usually exploit misconfigured and already exposed devices, yet this trend nevertheless highlights the growing diffusion of cyber threats interested in targeting physical processes.
The Opportunity Ahead
Despite a variety of nascent cyber threats, it is vital that maritime organisations are not paralysed. With knowledge of the maritime threat landscape comes a clear opportunity to proactively develop response and mitigation strategies. For instance, with a multitude of attacker techniques and relevant security controls, ensuring cyber risk assessments account for and respond to active sector threats will enable organisations to focus on the right areas.
This will be particularly important in the context of a maritime sector that is rapidly digitalising processes and systems to improve optimisation. This will likely include an increase in both remote and real time monitoring, as well as the maintenance of operational and safety systems. While increased visibility and monitoring opportunities are beneficial from a security operations and risk management perspective, it simultaneously widens an organisation’s attack surface.
Several challenges exist for the sector in building threat-informed strategies. There is plenty of catchup to do with cyber threat intelligence typically less integrated within maritime security functions when compared to other sectors such as financial services or technology.
Widening attack surfaces in the sector also increase the importance of adopting a wide aperture when accounting for threats. This includes monitoring criminal forums and marketplaces where access to maritime networks and data may be sold.
The maritime sector has also historically struggled to share data on sensitive issues. Within cyber security, loose plans to merely share information rarely lead to tangible results. Instead, a more substantive discussion that includes agreement on the mechanics of sharing threat data is required and a conversation overdue within the sector.
Fortunately, adopting a threat-informed strategy does not require abandoning existing strategic approaches (that have typically centred around cyber risk within the sector). A more pragmatic approach is to leverage cyber threat intelligence as part of a broader cyber risk framework.
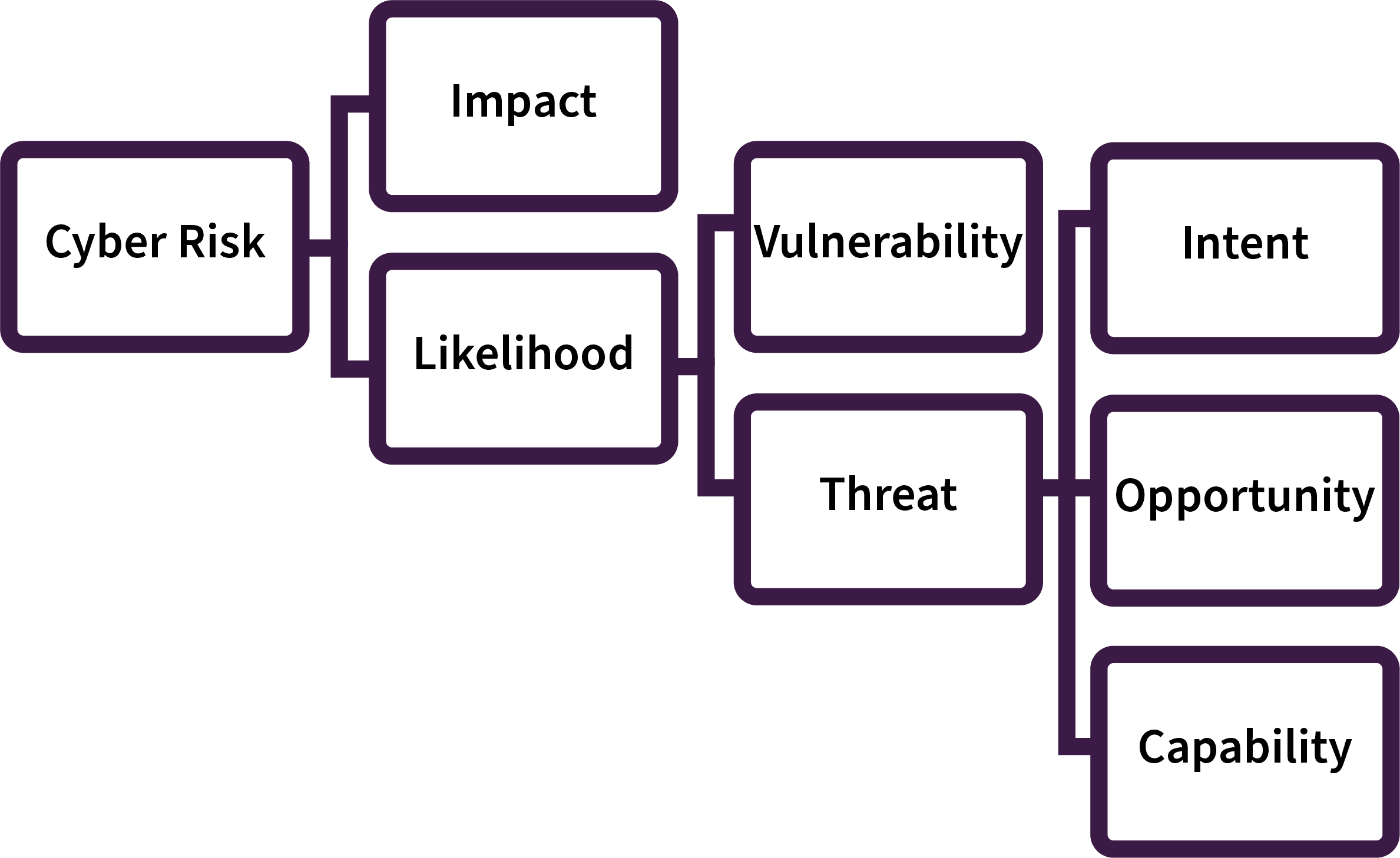
The diagram highlights how an understanding of maritime threats can form part of a wider risk strategy. Here, cyber threats intersect with organisational factors (such as the vulnerabilities of any systems used and the impacts of cyber attacks on business operations) to drive security decision-making.
By adopting such an approach, engagement with the cyber threat landscape can become a crucial enabler of security strategies. This will enable maritime organisations to stay ahead of the threat and capitalise on the full benefits of digitalisation.
WRITTEN BY
Dr Jamie Collier
RUSI Associate Fellow, Cyber and Tech


