Ransomware Now Threatens the Global South
Increased targeting of developing and middle-income countries by ransomware actors presents a challenge to political resilience, economic development and global cyber security.
A spate of ransomware targeting countries in the Global South has demonstrated an evolution in attackers’ tactics. Historically, ransomware has targeted a number of high-value sectors – finance, professional services, the public sector – in wealthy countries, concentrating on the US and other G7 members. Recent attacks on countries such as Costa Rica, South Africa, Malaysia, Peru, Brazil and India illustrate the increased threat to governments, critical national infrastructure providers and businesses in middle-income and developing countries. Ransomware presents a risk to these countries’ development, economic growth and political stability by disrupting commerce and the delivery of essential services. High-income countries have an economic and moral interest in ensuring ransomware does not create significant disruptions in middle-income and developing countries.
The Growing Global Reach of Ransomware
Ransomware, in which computer systems are compromised by attackers who subsequently demand a ransom for the restoration or non-exposure of encrypted and/or stolen data, has significant negative effects. Inability to access proprietary data, the risk of data exposure, and the total or partial shutdown of digital systems can cripple the normal delivery of goods and services.
Attacks on government agencies in Costa Rica between April and May 2022 demonstrate the impact of ransomware on small countries. The attacks, conducted by the Conti and Hive groups, crippled digital public services, resulting in paralysis in the tax and customs systems, disruptions to public sector pay, and large-scale theft of taxpayer data. The impact of the attacks led Costa Rican President Rodrigo Chaves to declare a national state of emergency, saying his country was ‘at war’ with the ransomware operators.
Figure 1: Map of Global Ransomware Victims
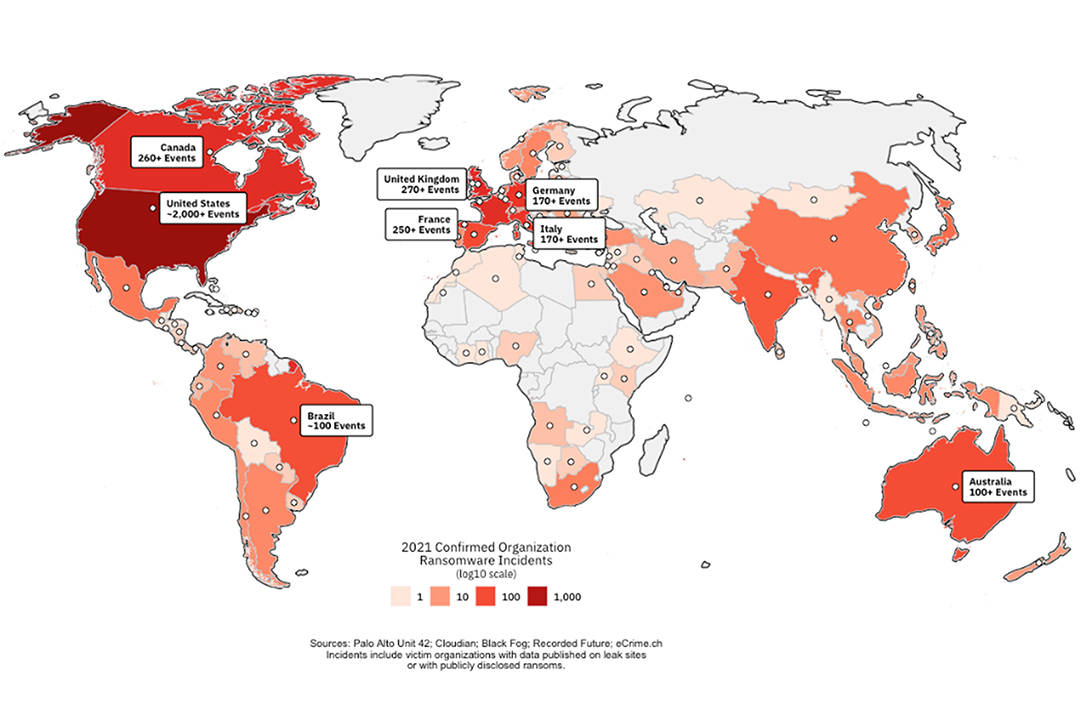
Ransomware is also a growing threat to larger middle-income countries (see Figure 1). In 2021, a major South African critical infrastructure company was targeted by ransomware, leading to the shutdown of several commercial ports and creating knock-on effects for global supply chains. Brazil has also increasingly been a target of ransomware, with separate attacks compromising IT systems and data at the Ministry of Health (impacting the availability of critical vaccine data), the National Treasury and Eletrobras, Latin America’s largest power company. Finally, there has been a spike in ransomware targeting India, including recent attacks on SpiceJet – India’s second-largest domestic airline – causing significant disruptions to flights, and Oil India, whose servers were compromised.
Explaining the Shift in Targeting
There are likely a number of push and pull factors that have incentivised ransomware operators to diversify their targeting to include more victims in the Global South.
Organisations in the Global South may be less able to engage in sanctions due diligence or to access some of the incident response and ransomware recovery services that enable organisations to resist paying a ransom
One explanation is that some ransomware operators' approach to selecting victims has become unacceptably risky and increasingly difficult. While many ransomware victims are small businesses, since 2019 some of the most prolific ransomware operators have engaged in so-called ‘big game hunting’ – human-operated ransomware campaigns against medium-to-large companies. High-value targets, disproportionately located in the US and other G7 countries, have faced large volumes of ransomware. Prominent ransomware attacks against US and European critical national infrastructure, in particular, have started to generate more forceful responses from US intelligence and law enforcement agencies. The FBI, for instance, has scaled up efforts to combat ransomware, including by seizing its proceeds: for example, it retrieved $2.3 million of the ransom paid in the 2021 Colonial Pipeline incident. The expanding scope of the US Treasury’s Office of Foreign Assets Controls sanctions regime targeting ransomware operators and the cryptocurrency infrastructure that supports their money laundering may also be reducing victims’ appetites to pay. Media reporting also indicates that sanctions related to Russia’s invasion of Ukraine have increased pressure on victims – and the insurers, lawyers and negotiators that support them – to engage in sanctions due diligence.
These actions may have altered the risk calculus of some ransomware operators, as suggested by a recent joint alert by US, UK and Australian cyber security, intelligence and law enforcement agencies. This may also be prompting a shift towards gaining or purchasing access to victims in developing and middle-income countries that are unable or unwilling to respond forcefully, thereby reducing the risk of blowback and unwanted attention.
Many developing and middle-income have historically poor levels of cyber security, owing to low dedicated expenditure. Consequently, organisations struggle to hire and retain skilled employees and often rely on legacy computer systems which have known vulnerabilities, or have low awareness of good cyber hygiene practices.
This has likely been exacerbated by rapid digitalisation in the Global South as internet penetration grows. The scale and pace of this change is particularly stark in the delivery of services related to commerce, financial services and health. The coronavirus pandemic has accelerated this trend due to efforts to create effective responses to health challenges. The introduction of new technology, however, has often outpaced the establishment of the kind of regulation and cyber security standards that could help manage new threats and vulnerabilities that arise. The result is an increasing amount of vulnerable internet-facing infrastructure and services that ransomware operators are able to compromise.
Why It Matters
The increasing breadth of countries being victimised by ransomware is not an isolated problem. Its direct impacts also have ripple effects, producing aftershocks throughout global commerce and governance. As the last two and a half years have demonstrated, global supply chain resilience is vulnerable to the kind of disruption that significant ransomware attacks can create. As a consequence, the disruption of physical and digital supply chains in the Global South also risks undermining the UK’s resilience.
The spread of ransomware to more countries risks fuelling the problem at a time when law enforcement operations and sanctions regimes in the US and Europe have started to have some success. If ransoms are paid, groups are incentivised to continue operating and can reinvest to fund operations against more governments and businesses. Organisations in the Global South may be less able to engage in sanctions due diligence or to access some of the incident response and ransomware recovery services that enable organisations to resist paying a ransom.
Given the heightened awareness of the threat posed by ransomware in developing and middle-income countries, the UK and its allies should expand their diplomatic activity on ransomware to include a broader and more diverse range of countries
Ransomware targeting countries in the Global South also indirectly affects the UK’s interests because it has the potential to destabilise partners’ political and economic resilience and threatens the positive dividends of digital development. With a looming global economic recession, food shortages created by Russia’s invasion of Ukraine, and continued supply chain disruption, the need to secure developing and middle-income countries against ransomware becomes more important in order to protect economic development.
Implications for UK and Allied Policymakers
Targeted and comprehensive assistance to develop cyber security capacities in at-risk and underserved developing countries is therefore needed. The UK and likeminded partners already engage with certain governments to promote cyber security; however, efforts are concentrated in ‘donor darlings’, countries which receive the vast majority of international assistance. Consequently, there is duplication of effort as agencies selectively compete to provide capacity building, and crucial issues in underserved countries are missed. Greater deconfliction and coordination would reduce the risk of duplication but, meanwhile, unilateral efforts by the UK would be more productively spent supporting underserved countries in prevention-, preparedness- and resilience-building activities.
In addition, the UK National Cyber Security Centre (NCSC) should expand the international assistance it provides to partner countries. The NCSC has a strong global reputation and engages frequently with advanced countries and select UK partners. By expanding its activities with smaller and underserved countries it can make strides in improving international cyber security, while advancing the UK as a supporter of a safe and secure cyberspace.
Given the heightened awareness of the threat posed by ransomware in developing and middle-income countries, the UK and its allies should expand their diplomatic activity on ransomware to include a broader and more diverse range of countries. This should aim to deepen operational collaboration to combat ransomware actors and the infrastructure that supports their activities. Doing so also presents an opportunity to highlight the Russian government’s willingness to provide a safe harbour for ransomware groups to middle-ground countries such as India, South Africa and Brazil. Given that Russia is actively seeking to court countries in the Global South following its invasion of Ukraine, these types of countries may be able to exert more influence on the Russian government to take action against the ransomware operators it tolerates and perhaps even encourages.
Conclusion
Ransomware and other cybercrimes are a central risk to digital, economic and political development. As digitalisation continues at speed, more essential and commercial services will rely on digital platforms and networks. This offers opportunities for our economies and societies, but only if we properly mitigate and prepare for cyber risks. Cybercriminals will continue to evolve, therefore so must we. Cyberspace is a global frontier; efforts which are nationally limited will not succeed. It is essential that countries with a head start in cyber give a helping hand to others. After all, a rising tide lifts all boats.
The views expressed in this Commentary are the authors’, and do not represent those of RUSI or any other institution.
Have an idea for a Commentary you’d like to write for us? Send a short pitch to commentaries@rusi.org and we’ll get back to you if it fits into our research interests. Full guidelines for contributors can be found here.
WRITTEN BY
Joseph Jarnecki
Research Fellow
Cyber and Tech
Jamie MacColl
Senior Research Fellow
Cyber and Tech
- Jim McLeanMedia Relations Manager+44 (0)7917 373 069JimMc@rusi.org



